

What we do
CoreDefense the digital world by delivering innovative security solutions & promoting cybersecurity awareness.


Vulnerability Management
Ingest vulnerability data from industry-standard scanners like Tenable.io and Nessus, with unified reporting and asset-level correlation for smarter remediation.


Vulnerability Management
Ingest vulnerability data from industry-standard scanners like Tenable.io and Nessus, with unified reporting and asset-level correlation for smarter remediation.


Vulnerability Management
Ingest vulnerability data from industry-standard scanners like Tenable.io and Nessus, with unified reporting and asset-level correlation for smarter remediation.


OT & ICS Security
Extend visibility into industrial control systems with Claroty integration. Aggregate IT + OT vulnerabilities and meet NIS2 / IEC 62443 compliance.


OT & ICS Security
Extend visibility into industrial control systems with Claroty integration. Aggregate IT + OT vulnerabilities and meet NIS2 / IEC 62443 compliance.


OT & ICS Security
Extend visibility into industrial control systems with Claroty integration. Aggregate IT + OT vulnerabilities and meet NIS2 / IEC 62443 compliance.


Cloud & DevOps Security
Secure AWS, Azure, and GCP environments with container monitoring and Kubernetes visibility. Deliver shift-left insights for DevSecOps.


Cloud & DevOps Security
Secure AWS, Azure, and GCP environments with container monitoring and Kubernetes visibility. Deliver shift-left insights for DevSecOps.


Cloud & DevOps Security
Secure AWS, Azure, and GCP environments with container monitoring and Kubernetes visibility. Deliver shift-left insights for DevSecOps.


ITSM & Workflow Automation
Integrate with ServiceNow, Jira, Slack, and Teams to turn security insights into action with automated assignments and escalation.


ITSM & Workflow Automation
Integrate with ServiceNow, Jira, Slack, and Teams to turn security insights into action with automated assignments and escalation.


ITSM & Workflow Automation
Integrate with ServiceNow, Jira, Slack, and Teams to turn security insights into action with automated assignments and escalation.


Compliance & Governance
Automate ISO, NIST, PCI DSS, CIS, GDPR, and NIS2 compliance. Generate real-time dashboards and audit evidence.


Compliance & Governance
Automate ISO, NIST, PCI DSS, CIS, GDPR, and NIS2 compliance. Generate real-time dashboards and audit evidence.


Compliance & Governance
Automate ISO, NIST, PCI DSS, CIS, GDPR, and NIS2 compliance. Generate real-time dashboards and audit evidence.

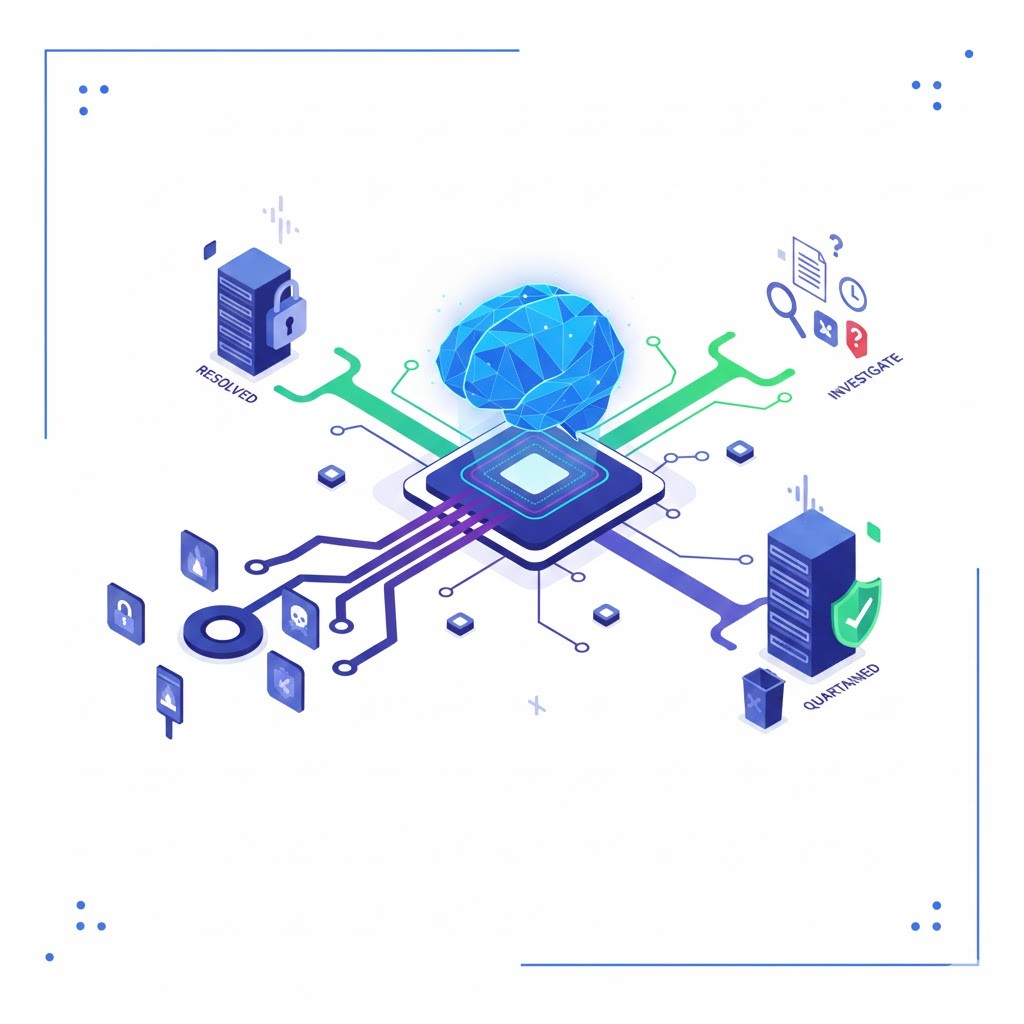
AI-Powered Threat Triage
Cut through noise with intelligent prioritization. CoreDefense highlights vulnerabilities that matter most to your business.


AI-Powered Threat Triage
Cut through noise with intelligent prioritization. CoreDefense highlights vulnerabilities that matter most to your business.


AI-Powered Threat Triage
Cut through noise with intelligent prioritization. CoreDefense highlights vulnerabilities that matter most to your business.


Business Process Mapping
Map end-to-end workflows to identify inefficiencies, optimize operations, and enhance audit readiness across teams and systems.


Business Process Mapping
Map end-to-end workflows to identify inefficiencies, optimize operations, and enhance audit readiness across teams and systems.


Business Process Mapping
Map end-to-end workflows to identify inefficiencies, optimize operations, and enhance audit readiness across teams and systems.


IT/OT Business Analysis
Unify IT and OT environments by assessing integration gaps and expanding security programs for improved resilience and compliance.


IT/OT Business Analysis
Unify IT and OT environments by assessing integration gaps and expanding security programs for improved resilience and compliance.


IT/OT Business Analysis
Unify IT and OT environments by assessing integration gaps and expanding security programs for improved resilience and compliance.


Security Business Analysis
Evaluate controls and workflows to pinpoint risks, close compliance gaps, and translate complex security needs into measurable value.


Security Business Analysis
Evaluate controls and workflows to pinpoint risks, close compliance gaps, and translate complex security needs into measurable value.


Security Business Analysis
Evaluate controls and workflows to pinpoint risks, close compliance gaps, and translate complex security needs into measurable value.
.faq & ans
Every single answer from here

What is the purpose of a VPN in cybersecurity?
Carnov is committed to providing exceptional car servicing solutions. With years of experience, cutting-edge technology, and a passion for excellence, we ensure your vehicle gets the best treatment.

What does "zero-day exploit" mean?
We deliver personalized solutions designed to meet the unique needs and objectives of each client. Our services range from website development and mobile app creation to digital marketing strategies.

What is phishing in cybersecurity?
We offer tailored solutions crafted to align with the specific goals and requirements of each client. Our expertise includes website development, mobile app design, and digital marketing strategies.

What is ransomware, and how does it work?
We create bespoke solutions tailored to each client’s unique objectives and requirements. Our specialties include website development, mobile app design, and innovative digital marketing approaches.

What is the purpose of a VPN in cybersecurity?
Carnov is committed to providing exceptional car servicing solutions. With years of experience, cutting-edge technology, and a passion for excellence, we ensure your vehicle gets the best treatment.

What does "zero-day exploit" mean?
We deliver personalized solutions designed to meet the unique needs and objectives of each client. Our services range from website development and mobile app creation to digital marketing strategies.

What is phishing in cybersecurity?
We offer tailored solutions crafted to align with the specific goals and requirements of each client. Our expertise includes website development, mobile app design, and digital marketing strategies.

What is ransomware, and how does it work?
We create bespoke solutions tailored to each client’s unique objectives and requirements. Our specialties include website development, mobile app design, and innovative digital marketing approaches.

What is the purpose of a VPN in cybersecurity?
Carnov is committed to providing exceptional car servicing solutions. With years of experience, cutting-edge technology, and a passion for excellence, we ensure your vehicle gets the best treatment.

What does "zero-day exploit" mean?
We deliver personalized solutions designed to meet the unique needs and objectives of each client. Our services range from website development and mobile app creation to digital marketing strategies.

What is phishing in cybersecurity?
We offer tailored solutions crafted to align with the specific goals and requirements of each client. Our expertise includes website development, mobile app design, and digital marketing strategies.

What is ransomware, and how does it work?
We create bespoke solutions tailored to each client’s unique objectives and requirements. Our specialties include website development, mobile app design, and innovative digital marketing approaches.
Ask more question. Get in touch
Ready to Strengthen Your Cyber Defense?
Experience the power of AI-driven security, automated compliance, and smarter remediation - all in one unified platform.